- Amazon VPC Subnets
- AWS VPC Route Tables
- IPv4 and IPv6
- Stateful AWS Security Groups
- Stateless AWS Network Access Control List (ACLs)
- AWS Internet Gateways (IGW)
- AWS Network Address Translation Instances and NAT Gateways
- IPv6 AWS Egress-Only Internet Gateways (EIGWs)
- Virtual Private Gateways, Customer Gateways, and Virtual Private Networks
- What are AWS VPC Endpoints?
- AWS VPC Peering Connections
- AWS Placement Groups
- Elastic Network Interfaces
- DHCP Option sets in Amazon VPC
- Amazon Domain Name Service Server
- VPC Flow Logs
- AWS VPC Tutorial Conclusion
This AWS VPC tutorial for beginners is a complete guide to providing you with information needed to understand how amazon cloud works. Amazon VCP is a networking layer that allows you to build your own virtual networks within an AWS Region. Here are some of the things that you can control in your environment:
- IP address range
- Create your own Subnets
- Configure route tables
- Create network gateways
- Control Security incoming and outgoing from your vpc and Instances
Prior to amazon vpc’s EC2 instances were launched into flat networks with other aws users. These types of environments are referred to as EC2-Classic and are no longer referenced. Any instances created after December 2013 are only created into a VPC environment. AWS creates a default vpc in each region with a default subnet in each availability zone. This aws vpc tutorial will go over the following Amazon vpc key concepts:
- Subnets
- Route Tables
- Ip Addressing
- Security Groups
- Network Access Control List
- Internet Gateways
- Network Address Translation Instances and Nat Gateways
- Egress Only Internet Gateways (EIGWs)
- Virtual Private Gateways (VGWs), Customer Gateways, and Virtual Private Networks (VPNs)
- VPC Endpoints
- VPC Peering
- Placement Groups
- Elastic Network Interfaces
- Dynamic Host Configuration Protocol Option Sets
- Amazon Domain Name Service
- VPC Flow Logs
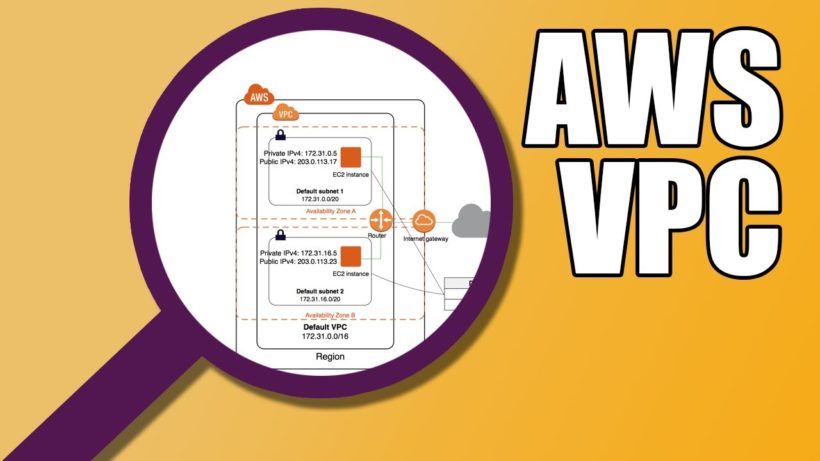
Amazon VPC Subnets
A subnet is a segment of a vpc that resides within a single availability zone. The subnet size is determined by the vpc ipv4 CIDR range. For example, if you create a vpc with a CIDR of 10.0.0.0/16, you could create multiple subnets of /24 or you could fill up the entire subnet with a /16. A subnet defined as /24 will have 251 available ip addresses because 5 IPs are needed for AWS.
Regardless of the type of subnet whether public or private, the IPv4 address range should always be a part of the private ranges. The defining distinction between a private and public subnet is the route to an attached internet gateway.
AWS VPC Route Tables
The route table makes routing decisions for a subnet. A route table can contain a set of entries that can define specific routing policies. Custom route tables can be associated with one or more subnets.
VPCs also contain a main route table that is used for all subnets that are not explicitly associated with a custom route table. Routes in a route table consist of a destination and a target. Targets can include Internet Gateways, NAT Gateways, egress-only Internet gateways (EIGWs), virtual private gateways (VGW), VPC gateway endpoints, VPC peers, and elastic network interfaces.
Route tables have one or more local routes with a target of local. These routes cannot be removed. Local routes ensure that resources have a route to each other. No route can be more specific than the local route. Routes have a route priority in this order:
- 1: Local route, even if a more specific route exists for the subnet
- 2: Most specific route (longest-prefix match)
- 3: Static routes are preferred over dynamic routes for equivalent prefixes
- 4: Dynamic routes propagated from AWS direct connect
- 5: Static routes configured on a VGW VPN connection
- 6: Dynamic routes propagated from a VPN
One last thing to remember when reading this aws vpc tutorial for beginners and dealing with route tables is:
- Your VPC has an implicit router
- The VPC has a main route table
- You can create additional custom route tables
- If you don’t explicitly associate a subnet with a route table it will use the main route table
- A custom route table can be set as the main route table so that new subnets are automatically associated with it
- AWS uses a predefined route priority to make routing decisions
IPv4 and IPv6
In order for resources to communicate with each other you must have proper subnetting and ip addressing in place. The IPv4 CIDR block you assign your vpc when created is a private range if Ip addresses. When needing to route to the internet you must assign either your vpc or instance a public IP address. Lets dig deeper into how IPv4 and IPv6 work inside of AWS.
IPv4 Addresses
Public IPv4 addresses are assigned from your CIDR block automatically or manually. Public IPv4 Addresses are controlled by amazon. When creating an EC2 instance, Amazon will provide a private IPv4 address at launch if one is not administered manually from your subnet block.
The private IP address on the primary interface is retained until an EC2 instance is terminated. Elastic IP addresses can be assigned automatically or manually to an instance that started up. An Elastic Ip address is a static, public IPv4 address that pulls from a pool that amazon manages. This then allows you to maintain a list of addresses that remain fixed for certain applications or servers depending on your needs. Here are a few important points to understand about Elastic Ip addresses:
- You must first allocate an Elastic Ip address within a VPC and then assign to an instance
- Also, Elastic IP addresses are region specific.
- Private Ip addresses and Elastic Ip addresses have a one-to-one relationship. meaning your instance will receive traffic destined to the private address mapping for your Elastic Ip address
- You can map Elastic IP Addresses from one private IPv4 address to another, either in same or different vpc, within the same region and account
- Your allocated elastic IP addresses remain with your AWS account until you explicitly release them
- And Last you are only charged for the Elastic IP addresses if its not assigned to a running instance
IPv6 Addresses
For Amazon AWS purposes and this aws vpc tutorial for beginners, you should understand Link-Local Addresses (LLAs) and GUAs when discussing IPv6. LLAs are addresses from the reserved fe80::/10 CIDR block. This is a required “on-link” address used for a variety of purposes such as DHCPv6 and Neighbor Discovery Protocol.
The LLA is only significant to the link, or VPC subnet the elastic network interface resides on. The LLA is converted into a EUI-64 modified format that essentially takes the 48-bit mac address of the network interface and flipping the seventh-most bit and inserting FF:FE into the address. To understand how that works in depth check out this article.
In order for IPv6 addresses to communicate with the internet Amazon must allocate you a /56 GUA (Global Unicast Address) CIDR block to your VPC. Then you can then allocate a /64 to your subnets. Similar to IPv4, there are two ways to assign an IPv6 address to your instances, Either automatically during launch or during the creation of the instance.
Stateful AWS Security Groups
Security groups are stateful firewalls that control inbound and outbound network traffic to AWS resources and EC2 instances. When an EC2 instance is launched and no security group is specified then it will be launched into the default security group for that VPC. Default security groups allow communication between all resources within the security group and allow all outbound traffic.
The default security group can be modified but cannot be deleted. Security groups are stateful therefore depending on the rules that you apply the return traffic is allowed. When adding rules to security groups the inbound rules apply to the source IP address.
There may be times when you need to peer with another VPC in the same region, doing so will allow you to reference the same security group IDs from the peer VPC. Changes are applied to the primary network interface when using security groups on an instance.
Here is a list of important key concepts about security groups:
- You can create up to 500 security groups per VPC
- Up to 50 inbound and outbound rules can be applied to each security group
- A network interface can have up to 5 security groups
- Security Groups focus on allow rules and not deny rules
- You can specify separate rules for inbound and outbound traffic
- By default no inbound traffic is allowed until you add an inbound rule to the group or create a separate one
- New security groups allow all outbound traffic which can be removed.
- Security groups are stateful meaning they can respond to allowed inbound traffic regardless of the rules applied.
Stateless AWS Network Access Control List (ACLs)
Network ACLs work on a subnet level and are stateless. Meaning return traffic is not automatically allowed when new rules are created. Network Access Control List process the lowest numbered rule first. AWS network acls have a final deny statement at the end that cannot be modified. VPCs are created with a default network acl that allows all inbound and outbound traffic. Custom Network ACLs will prevent inbound and outbound traffic until you provision otherwise.
Network ACLs can be setup with rules similar to security groups to provide an extra layer of protection. This prevents issues if a security group happens to be provisioned incorrectly. Here is a comparison between security groups and Network ACLs:
| Security Groups | Network ACL |
|---|---|
| Operates at the network Interface level | Operates at the subnet level |
| Supports allow rules only | Supports allow and deny rules |
| Stateful: return traffic is automatically allowed regardless of any rules | Stateless: Return traffic must be explicitly allowed by rules |
| AWS evaluates all rules to decide whether to allow traffic | Evaluates rules in lowest numbered order to decide whether to allow traffic |
AWS Internet Gateways (IGW)
In order to get out to the internet in your VPC you must attach an Internet Gateway and associate a default route in your route table to the IGW. Internet Gateways maintain the one-to-one mapping between private IPv4 addresses and public Ipv4 addresses. The following steps are required to create a public subnet with internet access:
- Create and attach an internet gateway to a VPC
- Create a default route 0.0.0.0/0 for ipv4 and ::/0 for ipv6 to the internet gateway
- Configure network acls and security groups rules to allow relevant traffic to flow
Although not the only way to gain access to the internet, without using a NAT gateway you will need a public Ipv4 or Elastic Ip address or GUA for Ipv6.
AWS Network Address Translation Instances and NAT Gateways
Instances that you launch into a private subnet will not be able to gain access to the internet. NAT Gateways are better than NAT Instances because amazon maintains availability and bandwidth leaving you with less administrative overhead. Private subnets will create a route to the nat gateway which provides many to one mapping of IPv4 translations.
NAT instances are not supported for Ipv6. Ipv6 use what’s called egress-only Internet Gateways. Here is a breakdown of NAT Gateways Vs NAT Instances:
AWS NAT Instances
NAT instances are amazon linux images that accept traffic from other instances in a private subnet. The NAT instance maintains a translation table with the state of the forwarded traffic in order to return response traffic.
To allow a NAT Instance to communicate with an Internet Gateway and allow instance to access internet resources the following must take place:
- Create a security group for the NAT instance with outbound rules that specify the needed internet resources by port, protocol and by IP address
- Launch an Amazon Linux NAT AMI in the public subnet and associate the security group with it
- Disable source/destination check attribute of the NAT instance.
- Allocate a public Ipv4 address with the NAT Instance
- Configure route table for private subnet to direct internet bound traffic to NAT instance
As your environment grows you must maintain the bandwidth requirements of the NAT instance and also the uptime and availability
AWS NAT Gateways
The better approach to gaining access to the internet for an EC2 instance is NAT Gateways. This AWS managed resource is simple to manage and highly available. Using a NAT Gateway is very simple and requires only a few easy steps:
- Create a NAT gateway in a public subnet
- Associate an Ipv4 Elastic IP address with a NAT gateway
- Configure a route table associated with the private subnet to direct internet bound traffic to the NAT Gateway.
NAT Gateways are the preferred way to provide internet access to instances that do not need to be directly accessed from the internet.
IPv6 AWS Egress-Only Internet Gateways (EIGWs)
Amazon does not support NAT for the Ipv6 protocol. Every Instance that’s provisioned for Ipv6 has at least one GUA. To gain access to the internet, an Egress-Only Internet Gateway must be created. Unlike a NAT Gateway or NAT Instance, an egress-only internet gateway does not perform address translations. The instance Ipv6 address is visible end to end.
Virtual Private Gateways, Customer Gateways, and Virtual Private Networks
In order to extend you existing datacenter to the cloud, you can establish either a hardware or software VPN connection. These three things are needed to create a VPN:
- Virtual Private Gateway: The VGW provides edge routing for your AWS managed VPN connections and AWS Direct Connect (which we will discuss later) The VGW manages routing separate from your VPC route tables.
- Customer Gateway: This device will sit on the remote end of the AWS VPN connection and must have a static IP address
- VPN Connection: The negotiated tunnel must be initiated by the customer gateway.
The VPN connection will consist of two IPsec tunnels for high availability. Also, if using static routing you must enter the routes for your network that should be communicating to the VGW. If using software VPN in your VPC then your EC2 instance must have a public IP address, be accessible from the internet with the correct ports enabled in the security group.
Here is a list of key concepts to understand about VGWs, customer gateways and VPNs from this aws vpc tutorial for beginners:
- The VGW is the AWS end of the VPN Connection
- The customer gateways is a hardware or software application on the customer side
- The customer gateway must initiate the VPN tunnel
- VGWs support dynamic BGP routing and static routing
- VPN tunnels consist of two tunnels for high availability
What are AWS VPC Endpoints?
VPC endpoints allow you to connect your vpc privately to supported AWS services using AWS Private link. This prevents the need for a NAT device, Internet gateway, VPN connection or AWS Direct Connect connection. There are two types of VPC endpoints:
- Interface Endpoints: Uses an elastic network interface with a private IP address to serve as the entry point
- Gateway endpoints: A route table target is created for a specified route to those supported services
Endpoints allow services in your VPC to use their private IPv4 addresses to communicate with resources outside their VPC. Resources in your VPC do not need public IPV4 addresses. Gateway endpoints support the following services:
- Amazon Simple Storage (Amazon S3)
- Amazon DynamoDB
Interface endpoints support:
- Amazon Kinesis Streams
- Elastic Load Balancing API
- Amazon EC2 API
- EC2 systems Manager
- AWS Service Catalog
- Endpoint services hosted by other accounts
- Supported Marketplace services
AWS VPC Peering Connections
VPC peering connections give you the ability to create network connections between two vpcs. Peering connections can be made with vpcs in the same region or to another region within the same amazon partition. Encryption between VPCs is provided by Amazon and a peering connection does not provide a single point of failure.
Peering connections are made using a request/accept method. The initiating VPC sends a request to the owner of the peer VPC. The Peer VPC has 7 days to accept the connection. Once an VPC peering connection is made both sides must add routes for the respective peer. Route entries will use the peer connection ID as the target.
Peering is a one-to-one relationship, meaning peering connections cannot have two peering agreements between them and do not support transitive routing. There are ways to get a connection to another VPC through one VPC but that’s outside the scope of this AWS VPC tutorial for beginners.
Security groups and DNS hostname resolution can be used when peers are established within the same region. When collaborating between VPC peers, they can provide many benefits to create a VPC Peering Connection. Here are some key points when considering using a VPC Peering Solution:
- You cannot create a VPC peer between VPCs with matching or overlapping CIDR blocks
- Peering connections are confined to the same Amazon partition
- Security groups can be referenced if in the same region
- You can use hostname resolution to receive private Ipv4 addresses
- Amazon handles encryption between peers in different regions
- Cannot have more than one peering connection between the same two VPCs at the same time
- For certain applications it may be more beneficial to use VPC endpoints
- Jumbo frames are supported between peers in the same region
- IPv6 supported only between peers in the same region
AWS Placement Groups
AWS placement groups allow you to group instances within a single availability zone. This provides low latency, high packet-per-second performance and high network throughput. Instance types with enhanced networking are recommended to be used when using AWS placements groups.
When planning you should start the number of instances that you need in a single launch. In the future you may run the risk of not having the needed capacity in the Amazon network where the placement groups reside. Here are some key factors to consider when deciding to use placement groups in AWS:
- Placement groups are confined to a single availability zone
- Network throughput is limited to the slowest instance
- Traffic outside of the placement group is limited to 25Gbps for Amazon EC2 and Amazon S3 in the same region.
- Placement groups support both IPv4 and Ipv6
Elastic Network Interfaces
Elastic network interfaces allow you to attach a virtual interface to an Instance in a VPC. Each interface has a Ipv4 private address, Mac address and at least one security group. You cannot detach the primary network interface but you can attach another interface that could reside in another subnet.
Although multiple interfaces cannot be used for NIC teaming, you can use multiple interfaces for various things such as network and security appliance use cases. Elastic Network Interfaces can be attached while running, stopped or at launch. The maximum number of interfaces depends on the instance type.
DHCP Option sets in Amazon VPC
DHCP is the standard for passing configuration host onto hosts on an IP network. Upon a VPC creation, Amazon creates a dhcp option set with two options:
- domain-name-servers: defaults to the amazon provided DNS
- domain-name: this defaults to the internal amazon domain name for your region
To assign your own domain name to your instances, create a custom DHCP option set and assign it to your VPC. The following values can be configured and each VPC must have exactly one set configured:
- domain-name-servers: up to 4 ip addresses
- domain-name: specify the desired domain name (example.com)
- netbios-name-servers: specify up to 4 NetBIOS name servers
- netbio-node-type: set this value to 2
Amazon Domain Name Service Server
DNS provides a way to resolve a hostname to an IP address. Amazon VPC provides a integrated DNS server which is enabled by default. Using the enableDnsSupport attribute determines if the Amazon DNS server is enabled in your VPC. The enableDnsHostnames determines if EC2 instances receive hostnames.
The Amazon DNS server runs on a reserved IP address at the base of the VPC IPv4 CIDR range, hence why extra ip addresses are reserved. The server can be integrated with Amazon Route 53 private hosted zones and AWS directory Service.
VPC Flow Logs
Amazon cloudwatch allows you to store IP traffic flow information in your VPC. These logs can be enabled at the VPC, subnet or network interface level. VPC flow logs are useful for a number of reasons such as anomaly detection and network troubleshooting. Here is a table of some of the flow log data elements that can be captured.
| Field | Description |
|---|---|
| Version | The VPC flow log version |
| account-id | The aws account id for the flow log |
| interface-id | displays the id of the network interface for which the log stream applies |
| srcaddr | Source IPv4 or Ipv6 addresss |
| dstaddr | destination ip address |
| protocol | The IANA protocol number of the traffic |
| packets | Number of packets transferred during the capture window |
| bytes | Number of bytes transferred during the capture window |
| start | Time the capture started |
| end | The end of the capture window |
| action | Whether the traffic was accepted or rejected |
| log-status | A log status of Ok, NODATA, or SKIPDATA |
AWS VPC Tutorial Conclusion
As you’re reading this aws vpc tutorial for beginners you may want to take time out and practice hands on what some of these features do. This guide here will walk you through creating an entire Lab in AWS. Amazon VPCs allow you to create your own private network Within the AWS Cloud. The cloud has helped many companies scale.