As you start to grow you will become more inclined to learn more of the advanced virtual private cloud components. If you didn’t read our previous blog post on a high-level overview of AWS, it’s worth a read. Even if coming into AWS for a long period of time sometimes it’s great to keep a little refresher on hand.
We didn’t get into many of the aws best practices when it comes to dealing with certain types of endpoints. It may also be great at times to see an actual design in action. As we go through this complete advanced virtual private cloud guide, here are a couple of key concepts that we will go over:
- Amazon VPC endpoints
- IP address features
- Elastic Network Interface Features
- Design considerations for certain scenarios
Although we list best practice at times throughout this document, it’s always safe to make sure you follow what works best for you, your HomeLab, or company you work for.
VPC Endpoints
In networking and design the idea of least privileged access has been around for a long time in IT. Giving the least amount of privileges to end users that they need can drastically improve security. AWS has done that with VPC Endpoints. VPC Endpoints allow you to give access to services such as amazon api, S3, Databases etc. When connecting to these services, your traffic does not have to leave amazon and does not require an Internet Gateway.
These endpoints are highly available and pose no problems to bandwidth constraints on network traffic. Here are some of the use cases for combining VPC Endpoints and Security into your environment:
- Security may have strict compliance policies on resources that can access the internet
- Define granular access control to services between VPCs or accounts without the broad access of VPC peering
- reduce the number of subnets that have internet access
- Reduce the need for NAT and routing policies
- Apply IAM policies to endpoints to control access from the endpoint to the services (does not replace or override user IAM policies)
Advanced VPC Endpoint Overview
Let’s compare the two types of VPC Endpoints that you can use to access services in AWS in more detail.
Gateway VPC Endpoints
Gateway VPC Endpoints allow you to create private connections between either Amazon S3 or an Amazon DynamoDB.
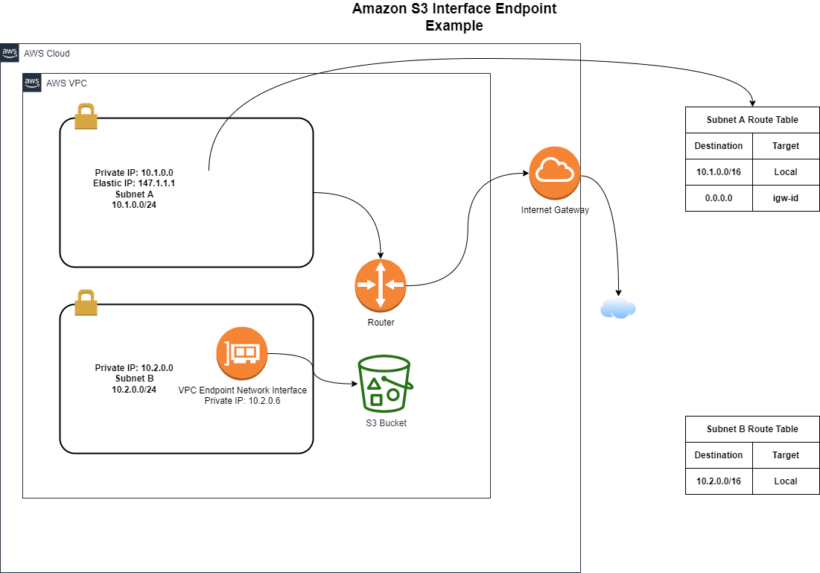
Amazon S3 Endpoints
An Amazon S3 endpoint allows private access to Amazon S3 from your VPC. As shown in the figure below you can see that subnet B when needing to access S3, its route table points to the prefix list directed towards the VPC Endpoint.
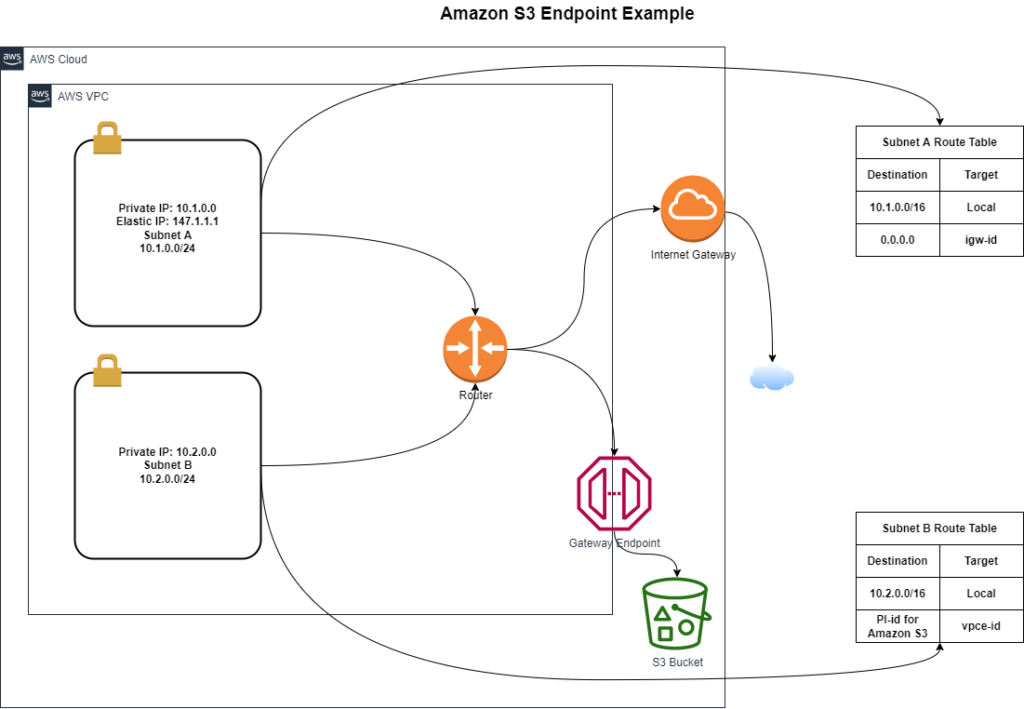
Multiple endpoints can be created in the same VPC. Different endpoint policies can then be applied for different levels of access. Route tables can only contain a single prefix list.
Amazon DynamoDB Endpoints
Amazon DyanmoDB endpoints use the same concepts as S3 Endpoints. Prefix list and route tables direct traffic to Amazon DynamoDB. Using endpoint polices, you can restrict access to operations such as writes or access to specific tables.
Configure Gateway Endpoints for Access over VPN and AWS Direct Connect
When using a gateway endpoint, the routing is done using route table entries and DNS to route traffic privately among AWS Cloud Services. This prevents access from outside of the VPC. One way to overcome this will be by following the steps below:
- Setup a VPN or Direct Connection from your datacenter to your VPC
- Setup an Elastic Load Balancer in your connected VPC
- Setup a Proxy auto scaling group to proxy the request coming from the load balancer
Now the corporate dns will map the request for s3.amazonaws.com to the elastic load balancer. This will solve the issue with the transitive routing because the request to the gateway endpoint will be from the elastic load balancer and not the outside network.
How to secure your gateway endpoints
You can limit the subnets with routes to the VPC gateway endpoint. Granular access per instance can be done by specifying the prefix list in an outbound security group rule.
Interface VPC Endpoints
Interface VPC Endpoints are a newer recently added approach to accessing service using local ip addresses in your VPC. This simplifies routing and allows for more flexibility. Interface endpoints will show an elastic network interface in your VPC. Access over Direct Connect to interface endpoints are allowed, supporting connectivity outside of your VPC. The following are some key considerations when connecting to services using Interface VPC endpoints:
- A VPC endpoint can only be accessed across an AWS Direct Connect connection and not through VPN or VPC Peering
- You can create one interface endpoint in all availability zones for each aws cloud service.
- Services for an interface endpoint may not be available in every availability zone
- Each endpoint can support a bandwidth off up to 10Gbps per AZ.
- Endpoints support IPv4 traffic only
- Endpoints can only return responses to traffic initiated from resources in your VPC.
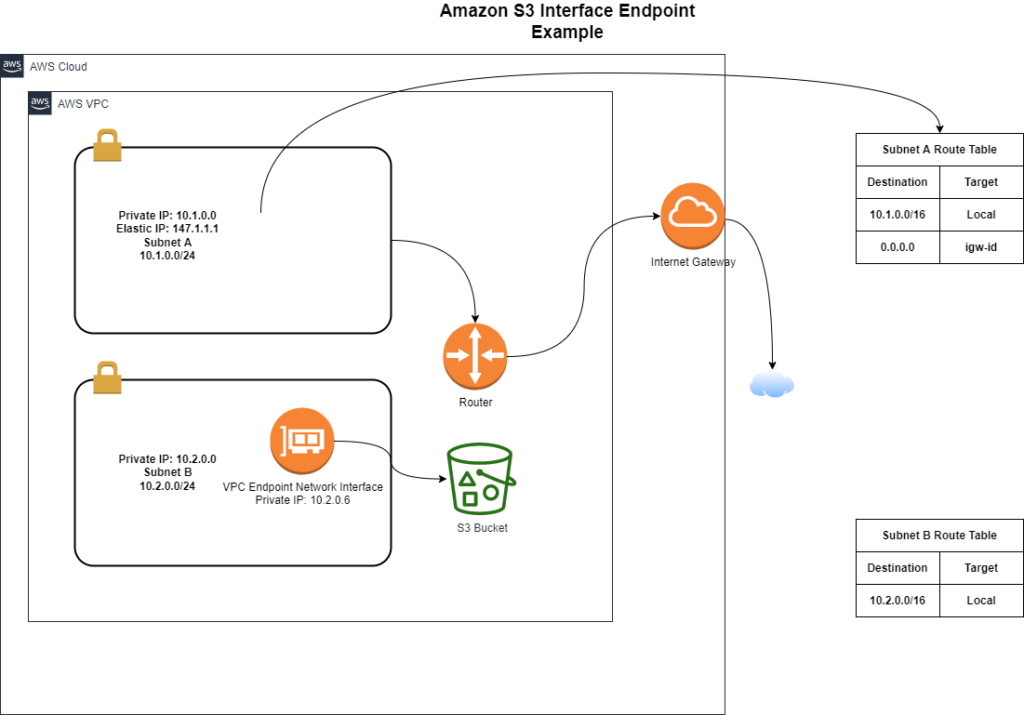
AWS PrivateLink for Customer and Private Service
Amazon Private link allows you to access or share a service securely between VPCs or accounts using a Network Load Balancer. Customers can build architectures and share applications between VPCs. Service providers can service consumer request through the network load balancer to the desired service they are looking to access.
This functionality can be useful for connecting applications across VPCs such as shared VPCs, connecting with business partners and customers.
AWS PrivateLink VS VPC Peering
As you start to build a more advanced Virtual Private Cloud, you may start to wonder if AWS Private link is better than VPC peering. VPC peering makes since when you have a lot of resources among both VPCs that need to communicate. Peering also makes since if there needs to be a high degree of communication between the two and the security trust are the same. There are 3 considerations that could be made when choosing using AWS Private link:
- First VPC peering allows access to the full vpc, which can be controlled by security groups and route table entries. If you only need to share particular services or resources then AWS PrivateLink reduces the complexity of needing to open up the entire VPC.
- Also when using peering you must have non-overlapping subnets. AWS Privatelink allows for overlapping subnets with the use of a network load balancer and the use of source nat.
- Third, a VPC can only peer with up to 125 other VPCs. AWS Private link can scale thousands of consumers per VPC.
Here are a couple of design considerations to consider when also looking to use AWS PrivateLink:
- The consumer can only originate connections to the provider.
- AWS PrivateLink traffic is load balanced.
- Connections from the consumer to the provider go through source nat which could prevent the application from identifying the consumer IP.
Service Provider Considerations for using AWS PrivateLink
When looking to configure the provider side of a VPC endpoint service here are the steps to consider:
- First you want to associate the network load balancer with your service.
- The load balancer is responsible for load balancing traffic, exposing a single IP per Availability Zone and performing source NAT
- If you create the load balancer first, create the service and associate with the load balancer
- Allow Access to the endpoint
Consumer Considerations for AWS PrivateLink
To start using an AWS Endpoint using AWS PrivateLink, you must start by requesting access to the private service by service name. Then configure DNS to reach the VPC Endpoint which can be done in many ways. Each VPC endpoint will have both a regional DNS name and a DNS name for each Availability Zone. If DNS is not supported or available, then hardcoded Ip addresses can be used in applications.
Accessing a Shared Service VPC
There are many scenarios where a shared resources VPC can make sense from a business standpoint. If your organization has a need to access resources across many VPCs, it may become helpful to put those common shared resources in one VPC.
Some of these shared resources may include authentication, provisioning, or security services.
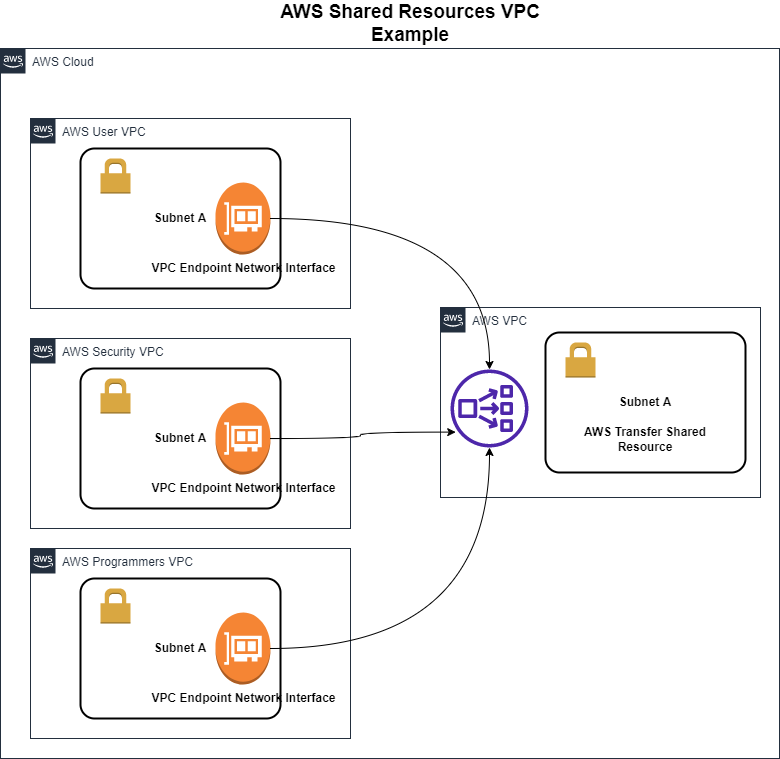
The above example shows 3 VPCs attached to a Shared resource Network Load Balancer using its Endpoint Network Interface. This model scales to thousands of consumers VPCs attached and possibly having overlapping IP addresses and not affect the other VPC connectivity.
AWS Transitive Routing
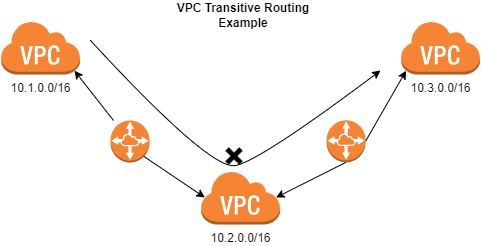
One of the security benefits that VPC provides is that it checks the source and destination Ip address to prevent address spoofing. If needing to be able to talk across other VPCs within AWS a more flexible connectivity solution will need to be introduced. Proxies, Routers, EC2 and NAT instances can provide more flexible routing options.
In the case of the picture above you can see that transitive routing is not allowed across the VPC environments. This is blocked because the source and destination are not of the same VPC environment and coming across another VPC peer.
A way to solve transitive routing scenarios is to use instances in each VPC to proxy or forward the traffic by providing a local network interface as the destination for remote networks.
IP Addressing Features
One of the first design considerations you must make when creating an AWS Advanced Virtual Private Cloud is the IP Scheme. AWS recommends starting with a Large CIDR range to avoid having to redesign in the future. If allocating to a large number of VPCs, you may have to keep the overall size into consideration.
Amazon allows you to resize and add up to 5 additional IPv4 CIDR ranges to your VPC. Here are some considerations you must look at when looking to resize:
- New CIDR ranges cannot overlap with existing CIDR range or any peers.
- The range must be more specific than and currently-defined static routes in the VPC route tables.
- Dynamic propagated routes do not conflict
Conclusion
In conclusion, to going over some of the more advanced features of AWS VPCs, hopefully you have a better grasp of some of the Advanced Virtual Private Cloud components. Some of these features may not be utilized by all customers but they are very important to understand. When you get a chance check out more of Amazon’s Documentation on the various services listed above.