If you are here you probably already know about the log4j vulnerability that has plagued the internet the past week. There are known applications that use this apache logging utility and Vmware Vcenter is one of those. I am going to show you Step by Step how to apply the VMWare log4j workaround.
First if you are using vcenter high availability then you will want to disable that according to VMware’s recommendations here. You can apply the workaround using the manual steps in the link provided, but the easier steps can be followed using the supplied python script from VMware which can be downloaded here.
Applying Vcenter Log4j workaround
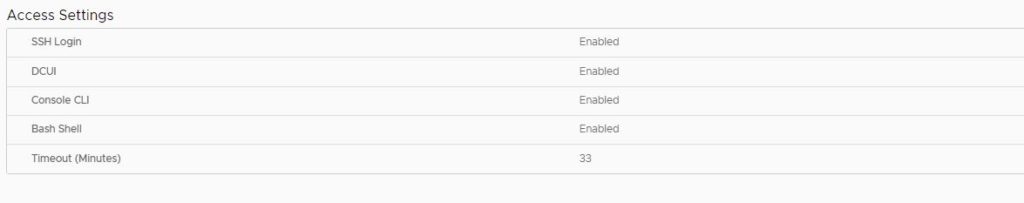
First you want to login to Vcenter https:vcenterurl:5480 and make sure that Bash Shell and SSH Login is enabled to be able to login as root.
Then using your ssh client of choice login to vcenter by going to the vcenter ip address and logging in as root and issuing the shell command.
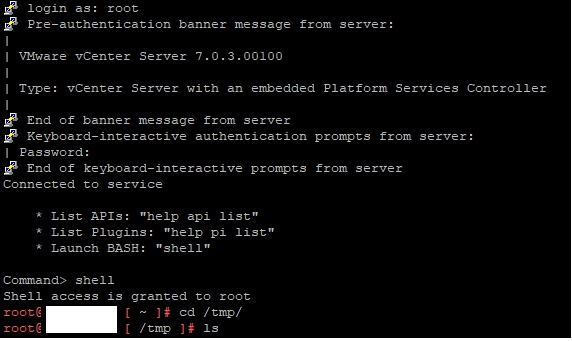
navigate to the /tmp folder and issue the command vi /vmsa-2021-0028-kb87081.py this will open an editor to be able to paste in the contents of the python script you downloaded above. Once inside of the Vi editor press the insert command on your keyboard. Then copy the contents of the python script into it by right clicking the screen.
(Press Esc and then type :wq! followed by Enter key) to save the contents of the file.
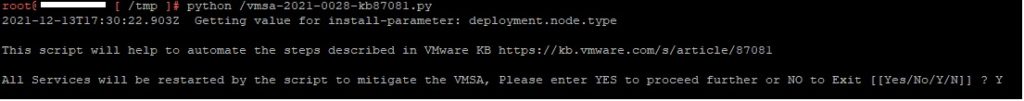
Execute the script by running python /vmsa-2021-0028-kb87081.py
the script will then ask you to approve. Enter Y
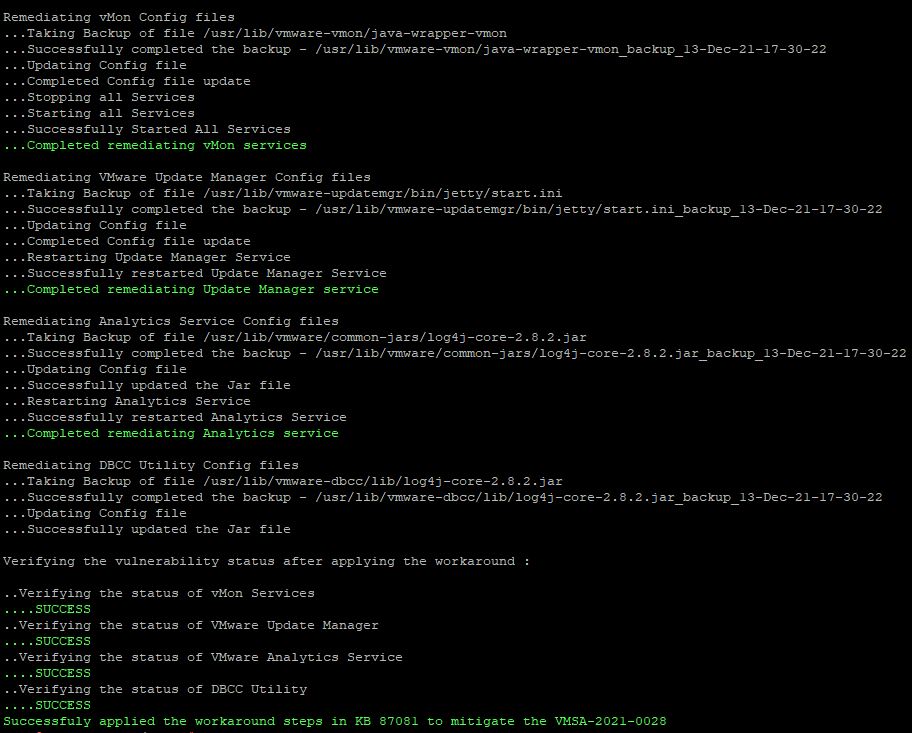
The script will proceed to go through the process up applying the workaround and you will be able to see the process finish through. Once successful you should see the prompt look like the picture below.