The AWS Site-to-Site vpn configuration is a setup most businesses using the cloud may come across. VPNs are needed to allow hosts to communicate privately over an untrusted network like the internet. A reason you may be reading this guide is to understand how this may benefit you.
Companies create AWS Site-to-Site VPN networks to allow on-premise devices to talk to servers or resources in the Amazon Virtual Private Cloud. VPNs can be set up using different protocols and technologies. The most common is called IPsec. Some other VPN technologies are DMVPN and GRE.
Let’s dive a little deeper into how a site-to-site vpn works and some of its design components.
AWS Site-to-Site VPN
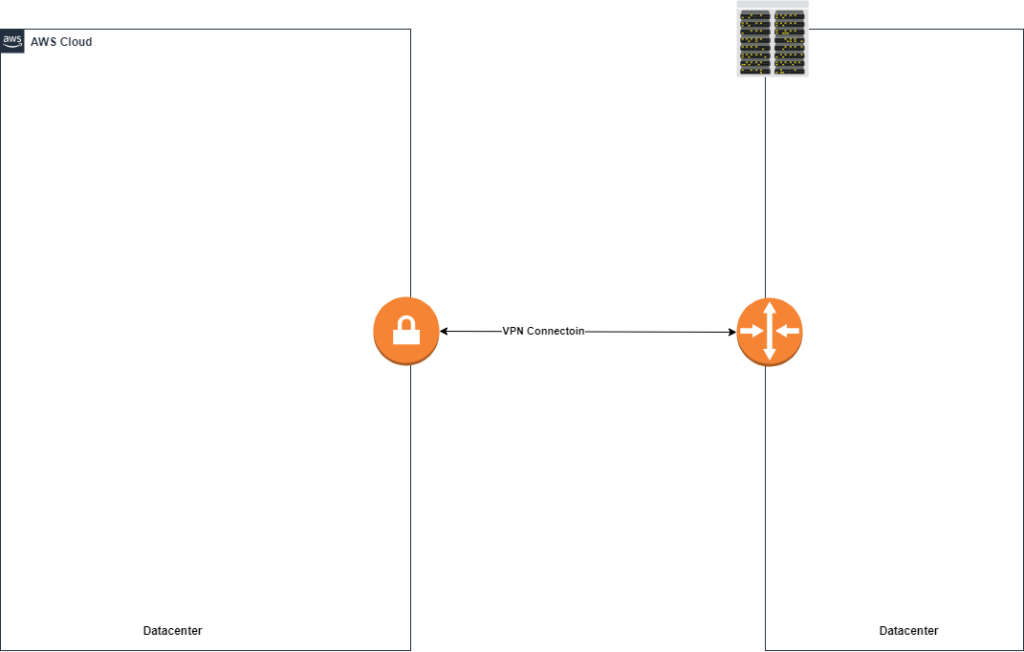
Site-to-Site vpns allow multiple sites to be able to talk securely over an untrusted medium such as the internet. These two sites can both be VPCs, Multiple Datacenters or VPCs in different regions. In order for two VPCs to create a connection to each other the following are required:
- VPN termination endpoint is required at each site
- The endpoint is responsible for running vpn protocols and associated packet processing
- All vpn traffic flow between the two sites is passed via endpoints
- VPN connection to AWS can only be used to access resources inside a VPC. This excludes services such as Amazon S3
- A VPN connection is required per VPC
Let’s discuss options available in needing to create an AWS site-to-Site VPN.
AWS VPN Termination Endpoint: Virtual Private Gateway
The Virtual Private Gateway (VGW) is a managed endpoint for your VPC. The Gateway can be created without an existing VPC and then attached to one after. The VPC must be in the same account and region. Each VPC can only have one attached to it at any point in time.
When creating a VGW, you will have the option to define an ASN number. The Autonomous System Number is for the AWS side of the external BGP session. BGP is used in route-based VPN connection to be able to use both tunnels and prevent asynchronous routing problems. After you have your VGW created you will get an output of information that you will use to setup the firewall on the Data Center Side.
VGW Availability and Redundancy
Amazon Virtual Private Gateway has built in redundancy and reliability from amazon. Upon the creation of a VGW, Amazon creates 2 highly available endpoints, each in a different Availability Zone. Configured VGWs have 2 tunnels that are configured with an IKE SA, IPsec SA and a BGP peering setup.
Some customer firewall devices use policy-based vpns and will create as many SAs as there are access control entries. VPNs that are configured this way will drop existing vpn tunnel connections when initiating a vpn tunnel that uses a different SA.
There are two ways to prevent the intermittent packet loss by:
- limiting the number of networks that can access the VPC from the customer network. Consolidate the networks into a single security association.
- Configure the policy to allow any network behind your vpn endpoint (0.0.0.0/0) which is generally the recommended approach.
AWS Site-to-Site VPN Features
For security, VGW supports the following cryptography suites:
- AES 256
- SHA 2
- Phase 1 Diffie Hellman groups: 2, 14-18, 22, 23, and 24
- Phase 2 DH groups: 1, 2, 5, 14-18, 22, 23, and 24
It’s important to also make sure that the endpoint on the other end is also configured to match the cryptography suites listed above.
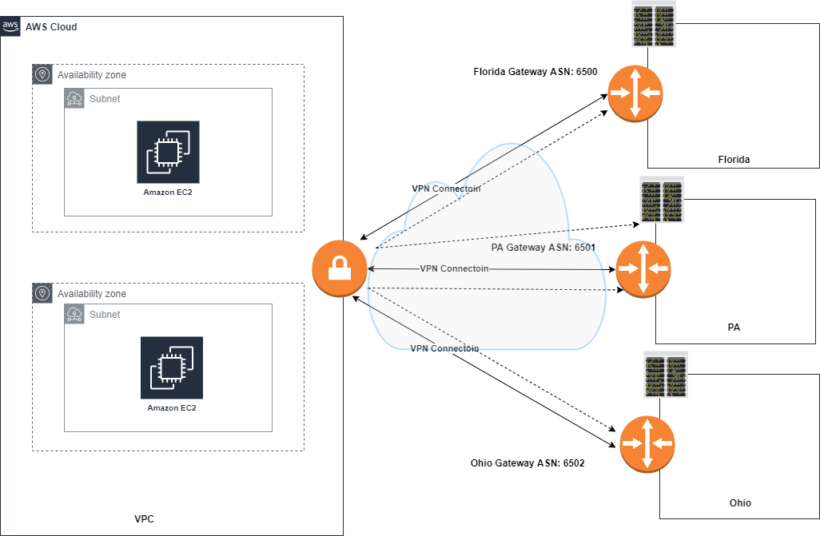
The VGW supports both static and BGP dynamic routing. BGP routing protocol allows your on prem devices to advertise multiple ip prefixes dynamically to the VGW using route advertisements. Amazon allows up to 100 propagated routers per vpc subnet route table. Its best to summarize as much as possible.
Within the VPC you can enable VGW route propagation to allow your VPC subnet route table to ingest routes learned by the VGW via BGP. The two tunnels that get created can cause issues of asymmetric routing and to mitigate this, amazon recommends you use the VPN tunnels in an active/standby mode using as-path prepends or MED BGP parameters like the picture below
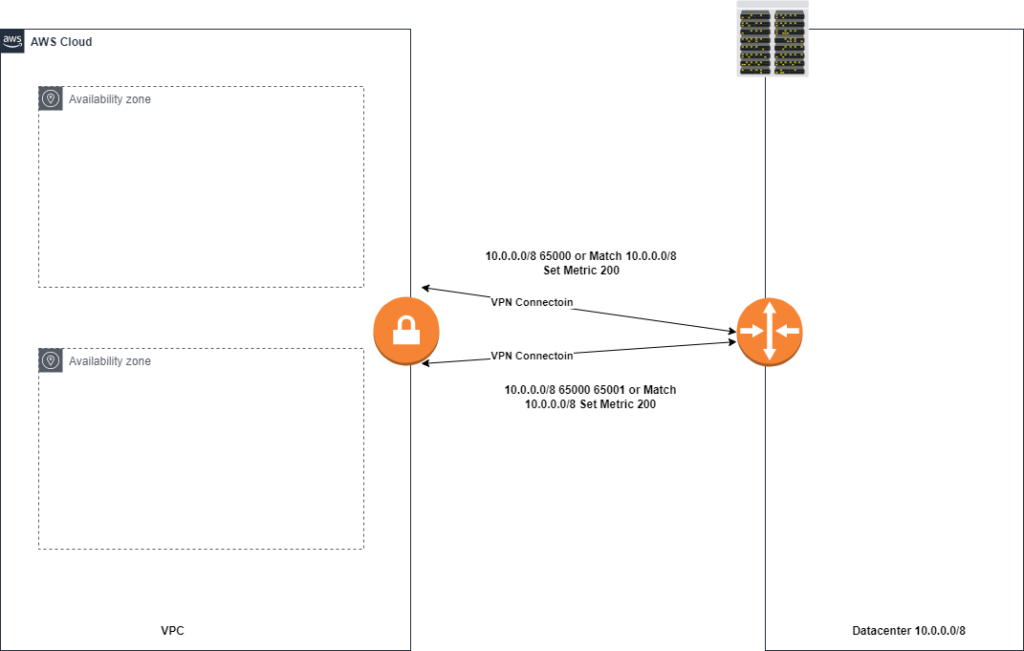
Amazon VPN Cloudhub
AWS VPN Cloudhub is a functionality that VGW supports, Cloudhub acts as a hub router connecting multiple remote branches together whether its attached to a vpc or not. This works great for AWS customers who have multiple branch offices and are looking for a low-cost hub and spoke backup connection between each remote office.
AWS Cloudhub has the following requirements and considerations when setting up:
- Must create a VGW and setup a VPN connection to all the sites you want to connect to Cloudhub
- Different or the Same BGP ASNs can be used depending on use case
- Customer gateways advertise the approprate routes (BGP prefixes) over the vpn connections
- Sites must not have overlapping ip ranges
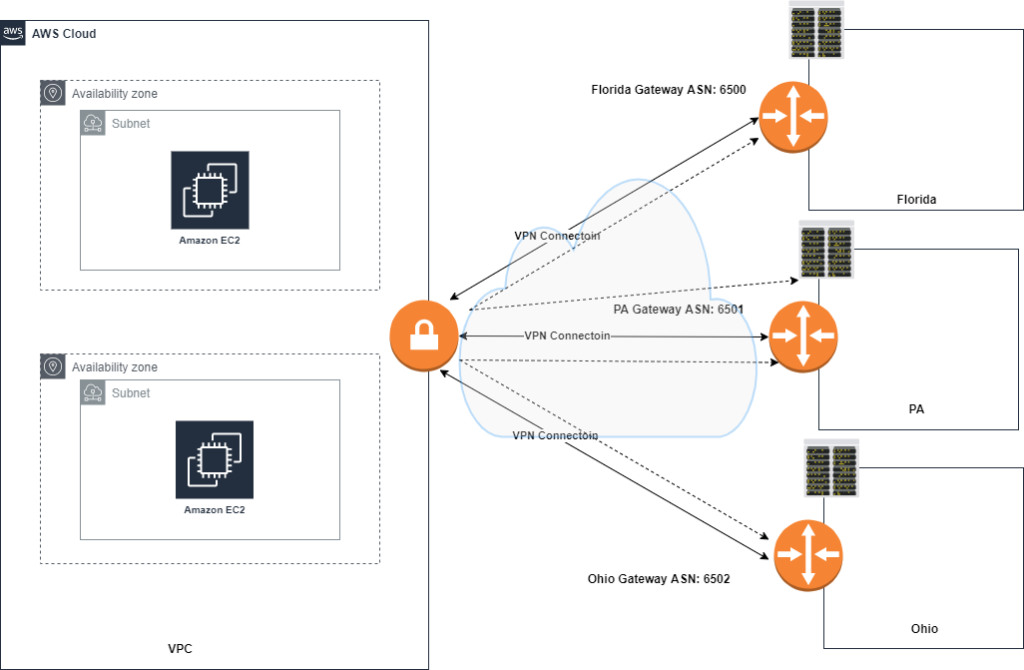
How to create an AWS VPN Connection
Creating a aws site-to-site vpn connection is really simple. When new to aws you can create a vpn connection using the console, making an api call or using cloudformation.
VPN is a managed service within AWS. The following details are entered during the setup and needed for VPN Creation:
- A created VGW to setup the vpn connection
- Customer gateway with the ip address of the vpn termination endpoint at the customer end
- Choose between one of two routing methods. Static routes or Dynamic BGP routes
- Using default aws tunnel configurations or custom values. Tunnels must be in the 169.254.0.0/16 range and custom preshared key.
The VGW ipsec parameters cannot be edited once the connection is created. You must delete the existing vpn and create new.
The AWS management console allows you to generate a configuration for your device automatically for many vendors. If your vendor is not listed you can download a generic config file.
Once created, this completes the creation of a vpn connection. The VGW has built in redundancy but it’s always best to have redundancy at the customer end as well as multiple endpoints. The VGW is not the initiator, the customer gateway must initiate the tunnels.
If the connection has a period of idle time, the tunnel may go down. AWS uses an on-demand mechanism to detect if the vpn is up or down.
Monitoring your AWS Vpn Connection
Amazon cloudwatch can be used to monitor the status of your VPN tunnels. Cloudwatch is a monitoring service that can be used for many AWS services. The metrics supported for vpn tunnels when using amazon cloudwatch are:
- TunnelState: captures the state of the tunnel
- TunnelDataIn: the bytes received through the vpn tunnel
- TunnelDataOut: Bytes sent through the vpn tunnel
View the latest amazon documentation to see the latest on monitoring your tunnels.
Alternate Amazon AWS VPN Creation Methods
An alternate to using the AWS VGW as your termination point is using a software provided EC2 instance. This option is usually chosen when:
- You need a special set of features on your termination point such as advanced threat protection or transitive routing capabilities.
- The need to run a different routing protocol such as DMVPN or GRE
- Supporting complex networking requirements such as overlapping networks
Availability and redundancy become your responsibility at this point when you go outside of using a VGW. The amazon marketplace has software from various vendors you can use to setup your firewall ec2 instances.
Conclusion
When it comes to securing your network and providing secure access from one datacenter to another, you will find yourself setting up a VPN tunnel at some point. The creation process is pretty straight forward on the Amazon side. I hope that you got a more in depth look into what goes into creating an aws site-to-site vpn.
If you are moving to the cloud and need to make this connection, first you want to create a secure aws account.