When building out your Amazon EC2 Instance, which we talked about more in depth in our previous article, you are responsible for configuring appropriate and effective access controls to protect your EC2 instances from unauthorized use. AWS provides four tools to help with these task such as:
- Security Groups
- Identity and Access Management (IAM) roles
- Network Address Translation (NAT) instances
- Key Pairs
Security Groups
An Ec2 security group plays the role of a firewall. By default, a security group will deny all incoming traffic. Group behavior will be defined by setting policy rules that will either block or allow specified traffic types. Traffic is assessed by examining its source and destination, the network port it’s targeting, and the protocol its set to use.
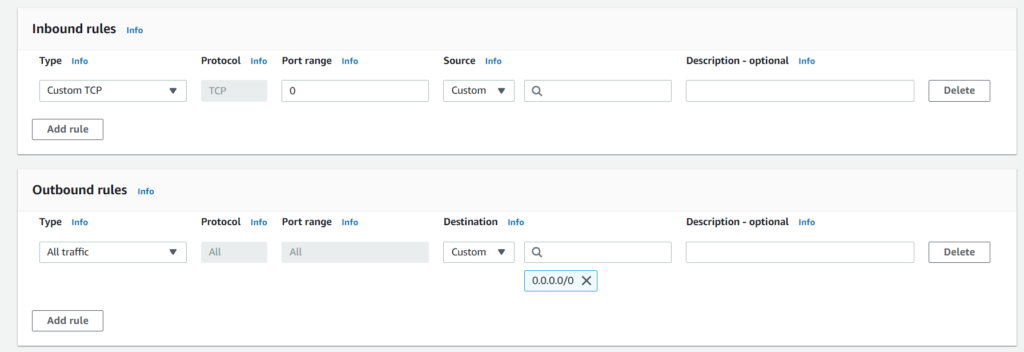
As you can see from the above picture security groups are created from a simple format. You have your inbound rules and your outbound rules. For instance if you want to allow “HTTPS” into your instance you will change your type to HTTPS. The protocol and Port range will automatically switch to the default settings. You will then have the option to choose your source as either IP address, or another security group.
Security groups can be applied only to instances in the region that it was created in. When making changes to existing security groups, those changes will be immediately applied to any instances the groups is applied to.
Amazon Identity & Access Management Roles (IAM)
Amazon’s Identity & Access Management Roles gives you the ability to control access to your AWS resources. An IAM role is defined by giving it permissions to perform actions on specified services or resources within your AWS Account. When a particular role is assigned to a user or resource, they’ll gain access to whichever resources were included in the role policies.
AWS IAM allows you to do a couple things that allow you to easily manage the security of your resources and accounts such as:
- Organize IAM roles and their permissions – Users can be created in IAM, and individual security credentials (such as access keys, passwords, and multi-factor authentication devices) can be assigned to them, or temporary security credentials can be requested to give users access to AWS services and resources. You can control which operations a user can conduct by managing permissions.
- Manage IAM roles and permissions — You can use IAM to define roles and manage permissions to control which activities the entity (or AWS service) that assumes the role can do. You can additionally specify which entity is permitted to perform the function. You can also delegate access to AWS services that create and manage AWS resources on your behalf using service-linked roles.
- Manage federated users and their permissions — Identity federation allows your enterprise’s current identities (users, groups, and roles) to access the AWS Management Console, call AWS APIs, and access resources without the need to create an IAM user for each identity. Use any SAML 2.0-compatible identity management system or one of our federation samples (AWS Console SSO or API federation).
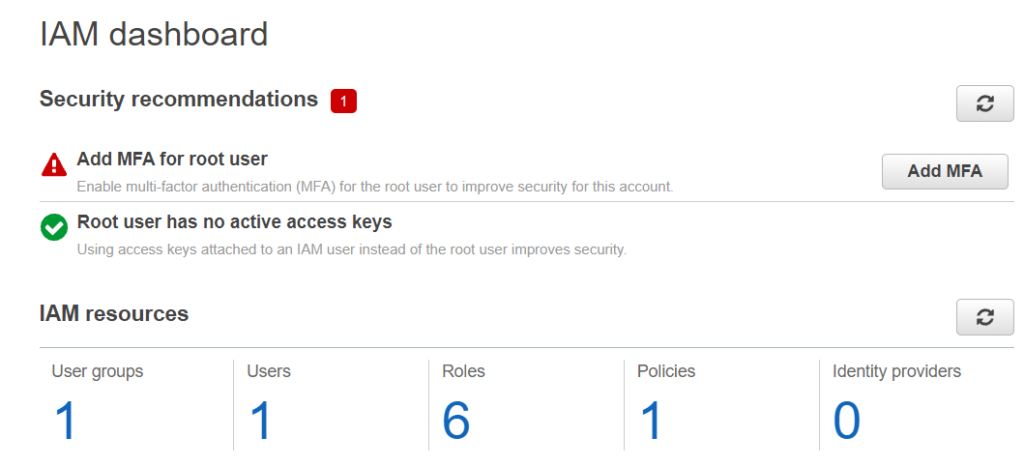
When you first sign into IAM you will get a picture like above that will show you your groups, users, roles, polices and identity providers that were created. Here is a list of best practices to follow to help keep your accounts and resources secure:
- Users – Create individual user accounts to prevent sharing of accounts and separate admin users from regular users.
- Groups – Manage permissions with groups to delegate the same permissions across a group of users.
- Permissions – Grant least privilege.
- Auditing – Turn on AWS CloudTrail to audit actions across the aws domain.
- Password – Configure a strong password policy for end users.
- MFA – Enable MFA for privileged users.
- Roles – Use IAM roles for Amazon EC2 instances.
- Sharing – Use IAM roles to share access.
- Rotate – Rotate security credentials regularly.
- Conditions – Restrict privileged access further with conditions.
- Root – Reduce or remove use of root.
Amazon Nat Devices
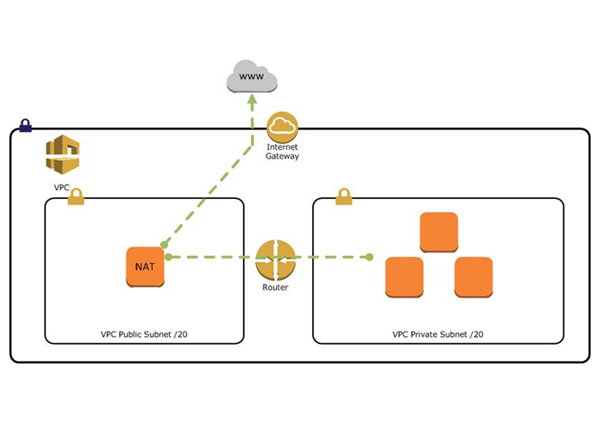
Sometimes you will need to configure an EC2 instance without a public IP to limit its exposure to the network. Without this exposure you lose access to the internet for this instance, which can cause a problem with receiving security updates. One solution is to route traffic between your private instance and the internet through a special device in your public subnet.
Aws gives you two ways to achieve this using either:
- AWS Nat Instance – These are built using an Amazon Linux AMI although you may use your own nat instance of choice as long as it can handle the bandwidth. Nat instances have things to consider when setting up which can be viewed here. The recommended option by AWS is to use a Nat Gateway
- AWS Nat Gateway – Nat Gateways are better because it provides more throughput, better connectivity and less management vs using an instance.
Amazon AWS Key Pairs
When initiating remote login sessions on running instances, you should never do it over unencrypted plain-text connections. To ensure that your connections are secure, you can generate key pairs and save the public key to your EC2 server, and save the private key half to your local machine. This method works for when using a linux host.
If working with a windows AMI, you will use the private key file to retrieve the administrator password to authenticate into your instance. Each key pair that AWS generates will remain installed within its original region and available for use with newly launched instances until you delete it. Its best practice to delete the AWS copy in the event your public key is lost or exposed. AWS allows you to have up to 5000 key pairs per region.