A fortigate firewall is a security device that a lot of businesses may find themselves using at the edge of their business locations. Your firewall may at times need consistent management when it comes to adding and removing firewall rules, creating objects, interfaces and more. This guide will walk you through how to setup your terraform to manage your fortigate firewall using terraform.
Creating your terraform api user
To be create a connection to your current fortigate, there are a couple of requirements that must be met. First we need to create a fortigate api user. Navigate to system, administrators, and select “Rest API Admin”.
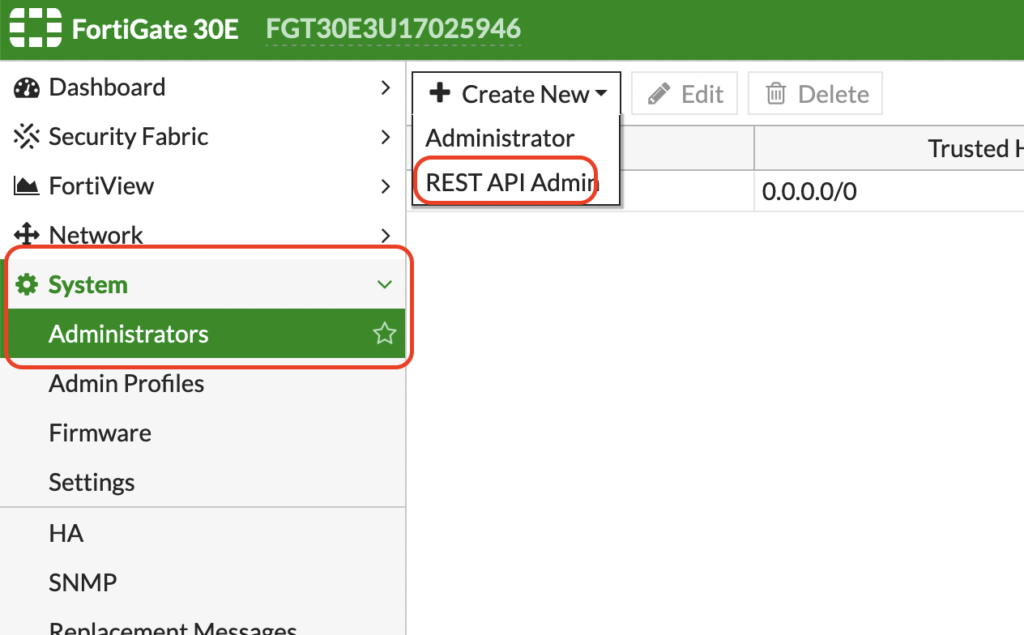
When creating a user we will need to setup a policy that gives this particular user read/write access to the firewall. If you were looking to only pull information from the firewall you could set it to read only access but we are going to give this particular account read/write.
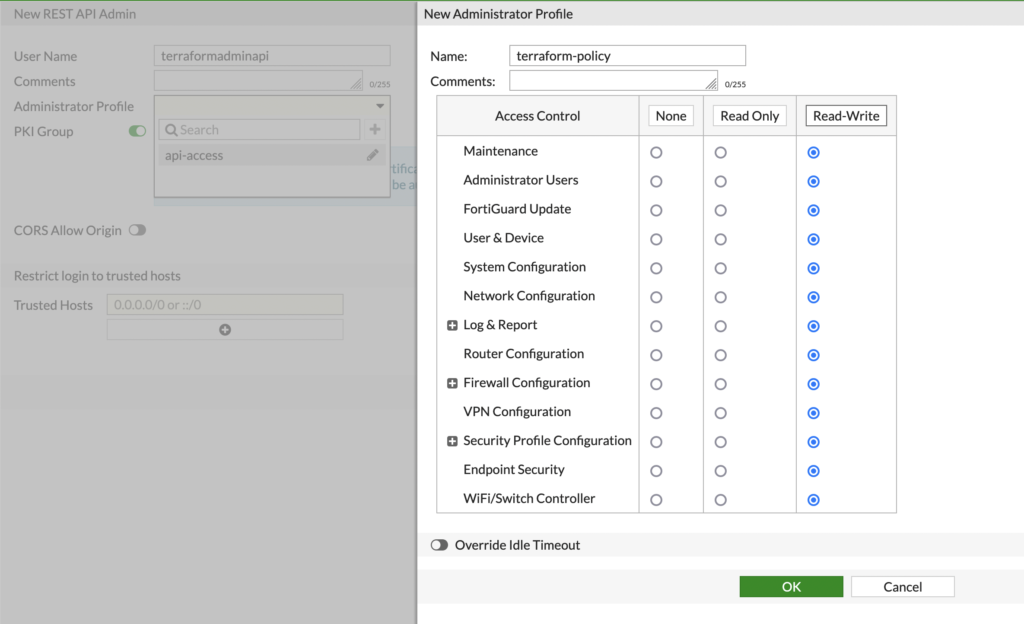
once finished with the policy, remove the pki group and add your ip address as a trusted host in the last input field.
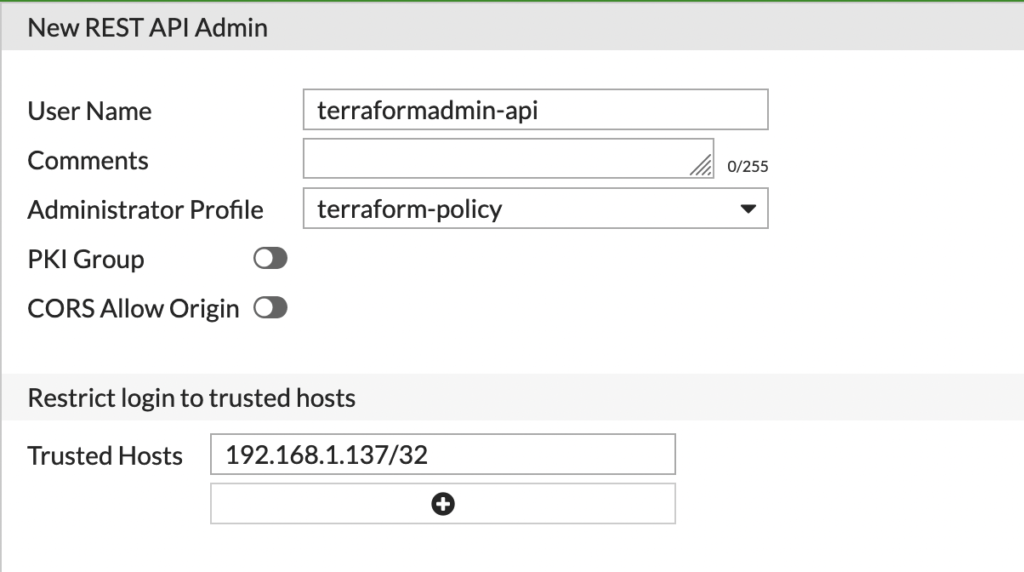
After you save the configured user, you will be prompted with an api key. You will need to keep this key to input into our terraform code.
Creating your fortigate terraform code
Once you have all the prerequisites in line, create a folder on your computer for your fortigate terraform files. To manage your fortigate using terraform create a file called main.tf in that folder. Paste the following code into your file:
terraform {
required_providers {
fortios = {
source = "fortinetdev/fortios"
}
}
}
# Configure the FortiOS Provider for FortiGate
provider "fortios" {
hostname = "<your ip address here to your gateway>"
token = "<your key here>"
insecure = "true"
}
resource "fortios_firewall_address" "main" {
allow_routing = "disable"
associated_interface = "lan"
color = 3
end_ip = "255.255.255.0"
name = "testaddress"
start_ip = "192.168.1.50"
subnet = "192.168.1.0 255.255.255.0"
type = "ipmask"
visibility = "enable"
}The fortinetdev/fortios is the terraform provider managed by fortinet that provides you access to the required resources needed to create fortigate resources. We’ve added a resource called fortios_firewall_address. This will create an object called testaddress. To test and make sure this works run terraform plan. If you have an error in your configuration for the api user you will get a message like this:
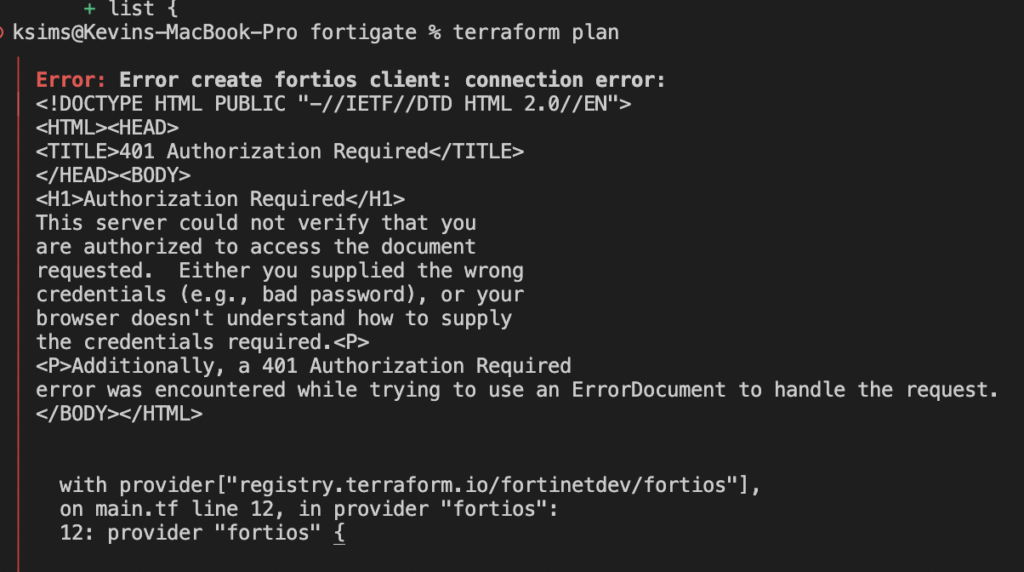
a successful plan and connection to your fortigate should reveal this
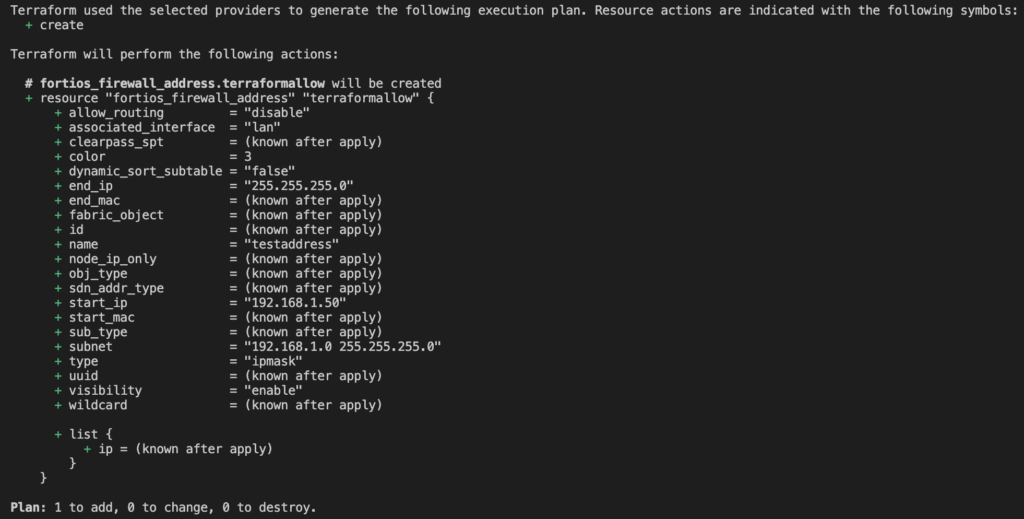
Now when we go back to the console in fortigate and will see our newly created address object
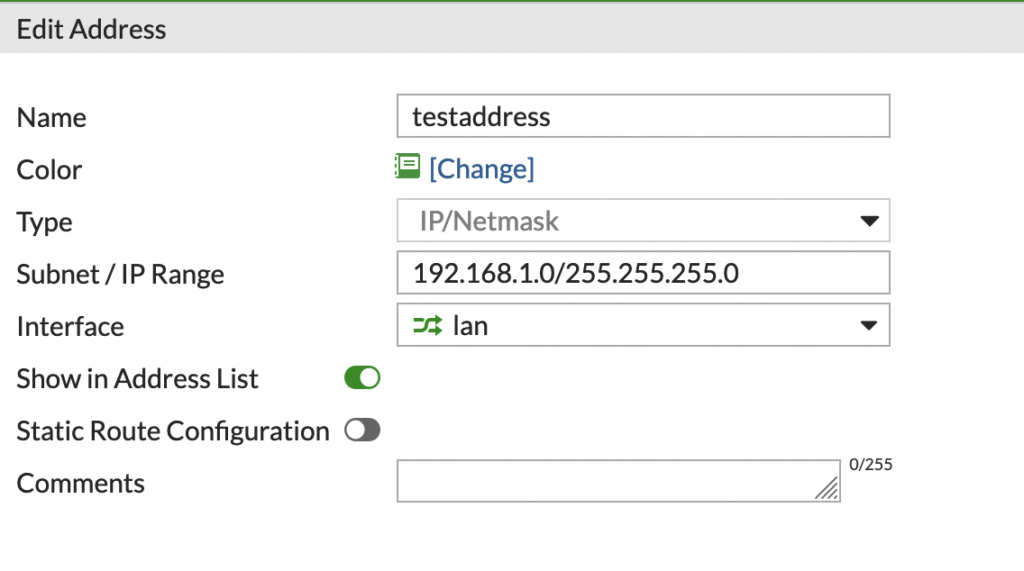
Now going forward you can manage your fortigate firewall using terraform. This will give you the ability to make quick changes to your firewall and revert changes a lot quicker if needed as well.
Conclusion
We have down deployed and can not manage our firewall using terraform automation. Another great solution to this is giving access to only being able to update or modify changes in a way in which code reviewers would need to review the changes that are being purposed before they are applied. Additional documentation can be found on terraform website here.