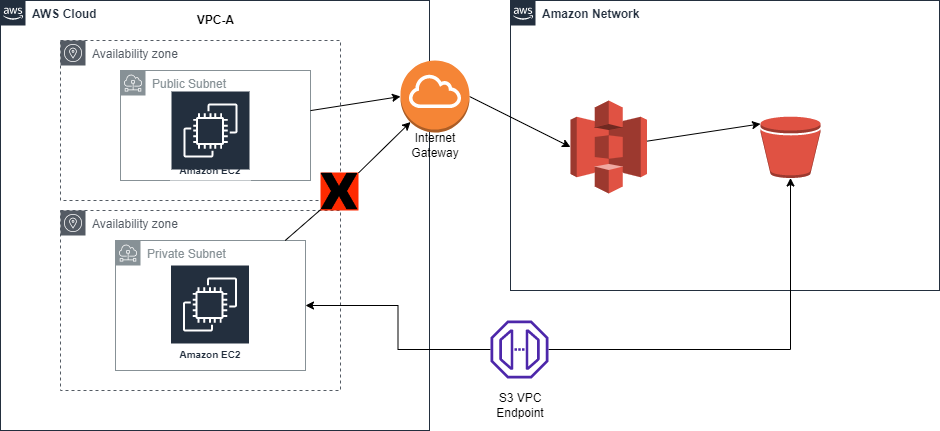
An aws s3 vpc endpoint allows private access to Amazon S3 from your VPC. This improves overall security since traffic to S3 will not have to go over the public internet. An example of this if if you have a private subnet that has no access to internet resources, traffic to S3 will be denied. When creating an AWS S3 vpc endpoint, you will allow for instances in the private subnet to then access resources needed like in the picture below.
If you already have an aws vpc environment you can skip to the creating an an aws vpc endpoint section. In this part of the tutorial we will walk through how to create an aws s3 vpc lab to access data privately.
Building an AWS VPC Lab to Test S3 Access
Create a New VPC
First we will need to create a new vpc. This tutorial assumes you do not already have one setup. Navigate to the aws console and click on Create VPC.
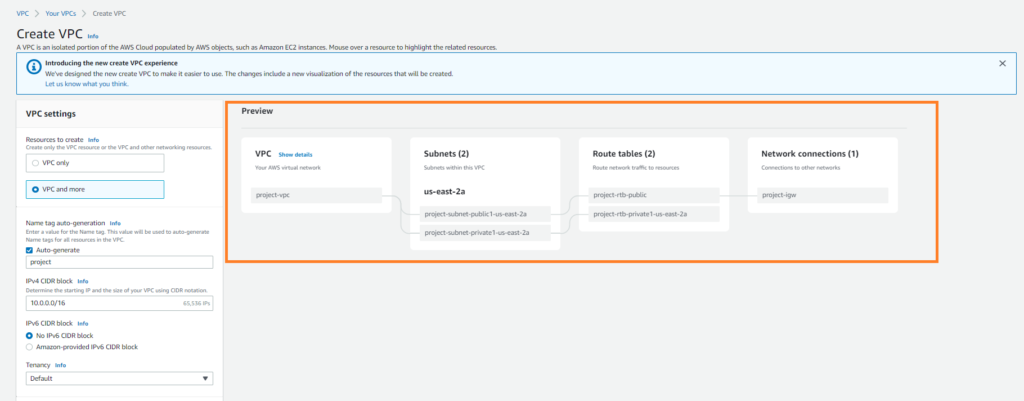
Using the Create VPC Wizard select the option for “VPC and More” and choose the following options:
- Ip CIDR Block: 10.0.0.0/16
- No Ipv6 CIDR Block
- Leave default tenancy to default
- 1 Availability Zone
- 1 Public & Private Subnet
- None for Nat Gateways & VPC Endpoints
Your vpc creation should look like the preview below.
Creating an S3 Bucket
Lets now create an S3 bucket that we can use to test with. Navigate to the S3 Console and click “Create Bucket”. Create a new bucket called “myprivatebucket” in your region of choice. Uncheck the Block all public access checkbox and click “Create Bucket” at the bottom.
Creating a role for s3 Access
In order to be able to access the service associated with the aws s3 vpc endpoint from an ec2 instance, we need to create a role that allows s3 access.
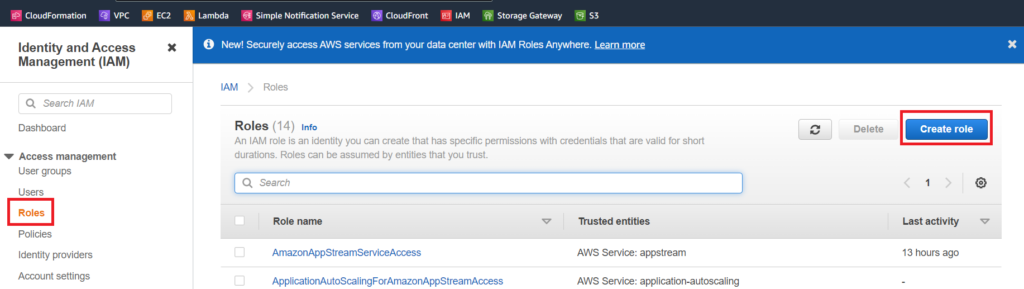
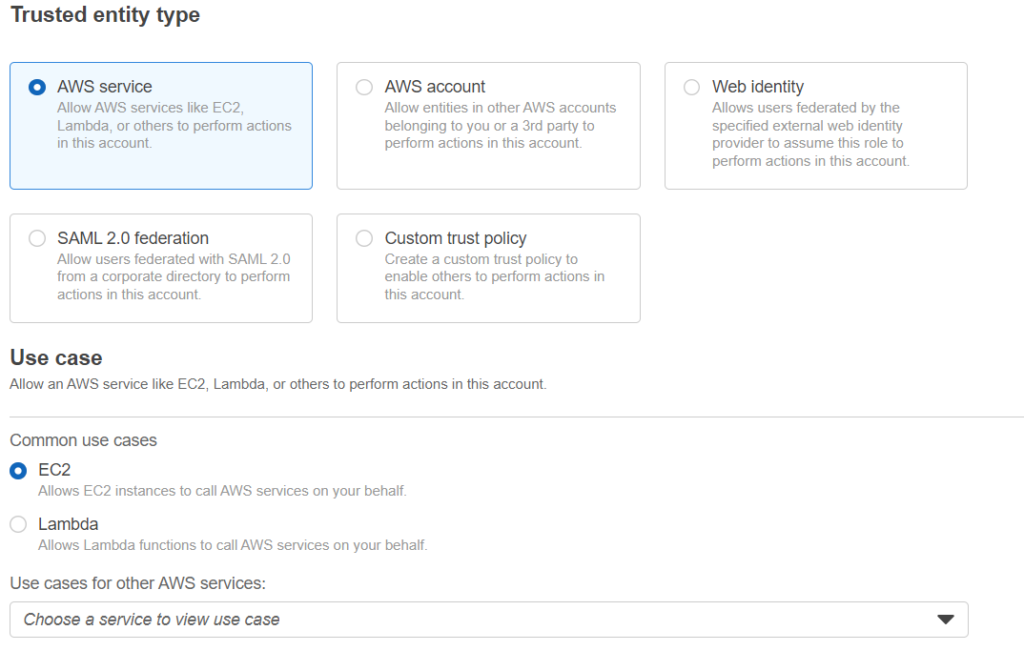
on the next screen look for the “AmazonS3FullAccess” role and check the box next to it. On the next page name the rule amazon s3 full access and save.
Launch Instances in Public & Private Subnets
Now that we have the vpc created, we need to launch instances in the public and private subnets. The private subnet ec2 instance will be used to test connectivity to s3 over the aws s3 vpc endpoint. The public instance will be used as the bastion host to connect to the private instance.
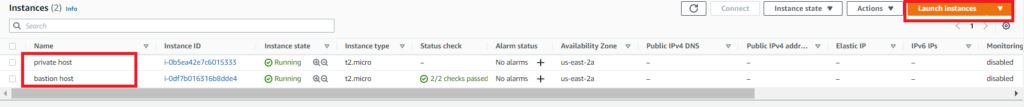
Using the launch instance button, Create 2 amazon linux instances. They offer a free tier which I am using for this demo. For the private instance create a security group that allows ssh access from the public subnet. When creating the public ec2 instance, create a security group that allows ssh access from anywhere.
assign the iam role we created above to the private ec2 instance when creating the instance.
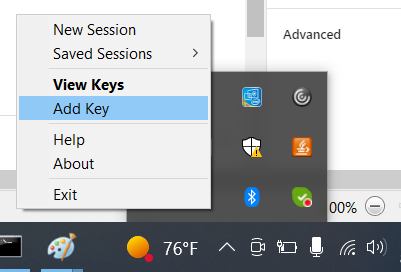
There will be an option to create a keypair. Download the keypairs .ppk key file and install the program pageant and putty here. Once pageant is installed and running. Right click the application in the bottom right hand corner of your pc. Click add key.
Testing AWS S3 Access
Now we need a way to access the public instance from the internet. On the public instance we will need to associate it with a public IP address:
- Go to the Ec2 console and select elastic ips
- Then select allocate elastic ip
- click allocate
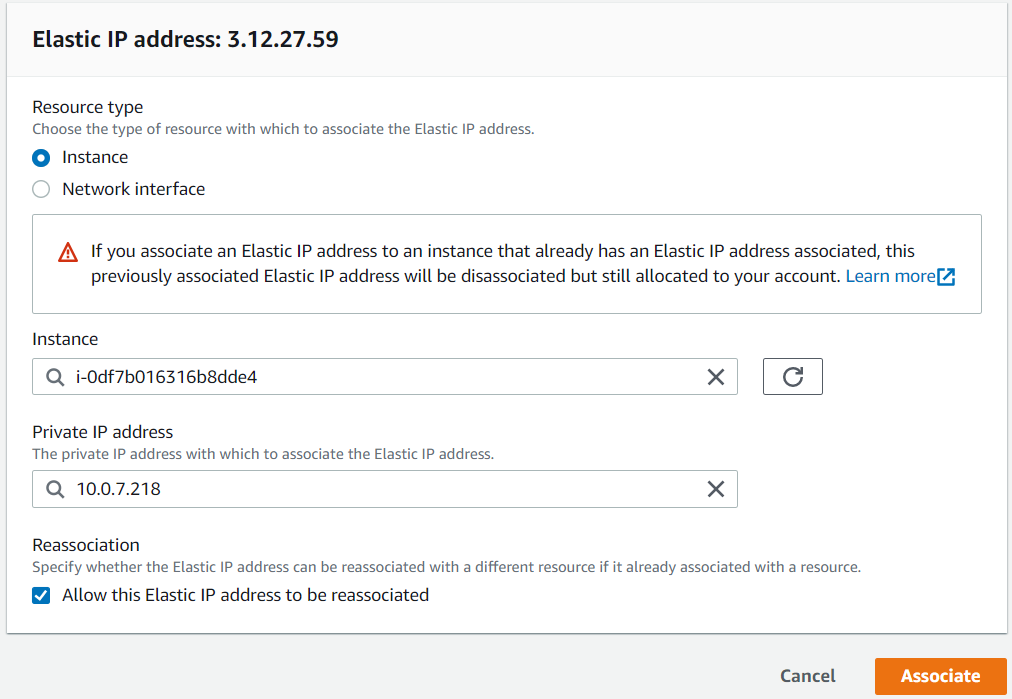
- after that select your elastic ip, click actions, then associate elastic ip
Your elastic ip should be allocated to the bastion instance itself.
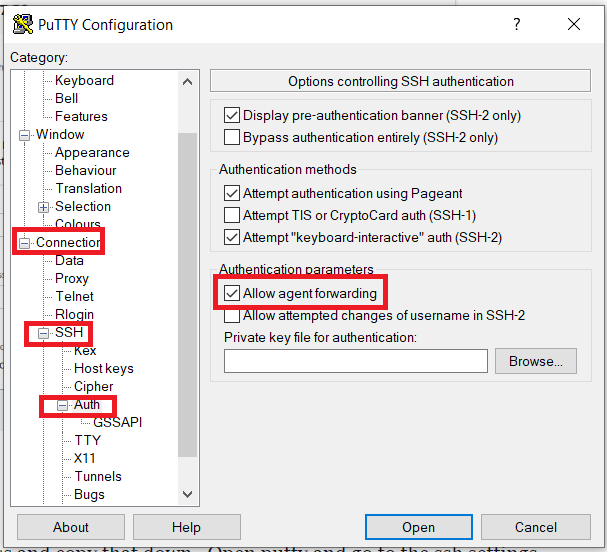
Once associated with your instance, take the public ip address and copy that down. Open putty and go to the ssh settings to enable agent forwarding. This is allows you to forward request through the bastion host to the private instance.
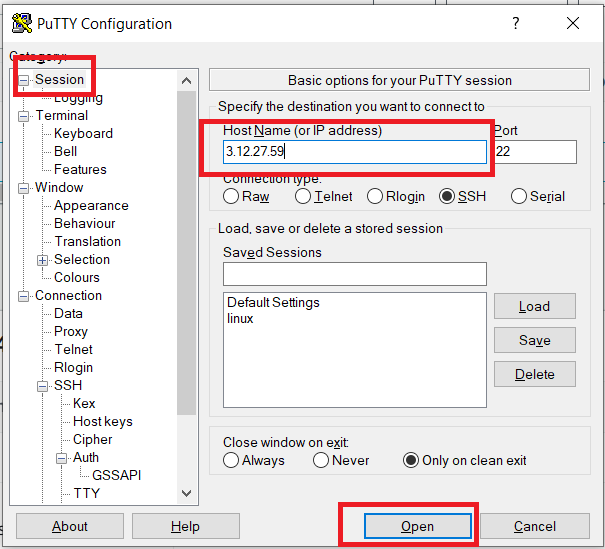
Then take the public ip address of the public instance and place inside of the putty session and click open.
Once you get logged into the public instance we need to test being able to access the internet and s3 from the private instance. The default user for the linux instance is ec2-user. Once we ssh into the public host, we can then run the command “ssh [email protected]” to ssh into the private host.
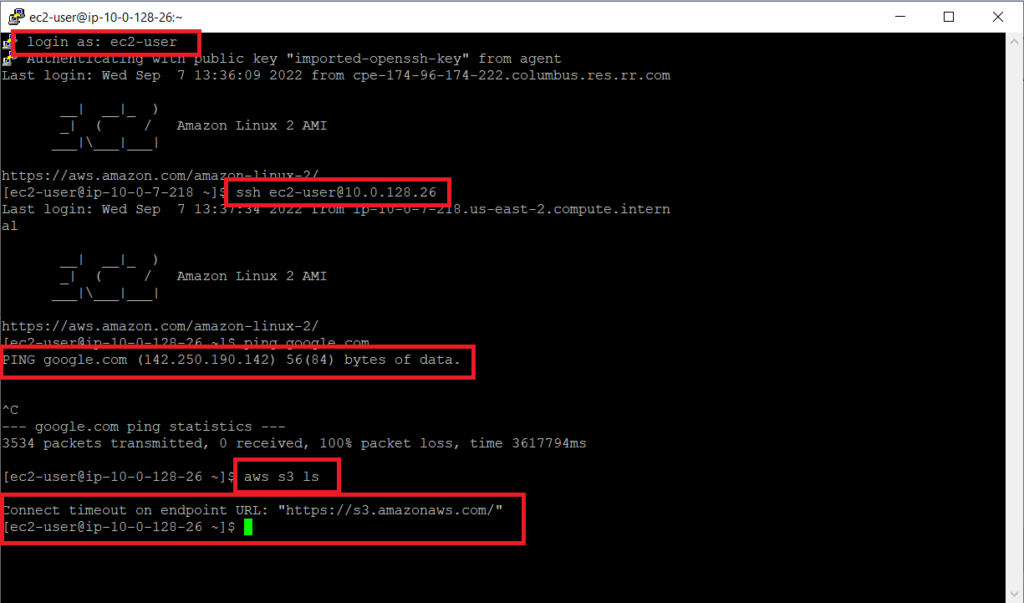
As you can see the public instance has no access to the internet to ping google and cannot access the s3 service even though we have the aws s3 full access role.
Creating an AWS S3 VPC Endpoint
Now we need to create an endpoint that the private instance can talk to. Click on the vpc console and on the left side select endpoint. Choose these options when creating an aws s3 vpc endpoint:
- Name your endpoint what you want
- choose aws services for the category
- type s3 in the service box and choose the gateway s3 service type for your region
- then choose the vpc that you want the endpoint associated with
- Select the route table you want the route applied to then select create endpoint
Now when we go back to our ssh console, we can now access the s3 bucket using the aws s3 vpc endpoint.
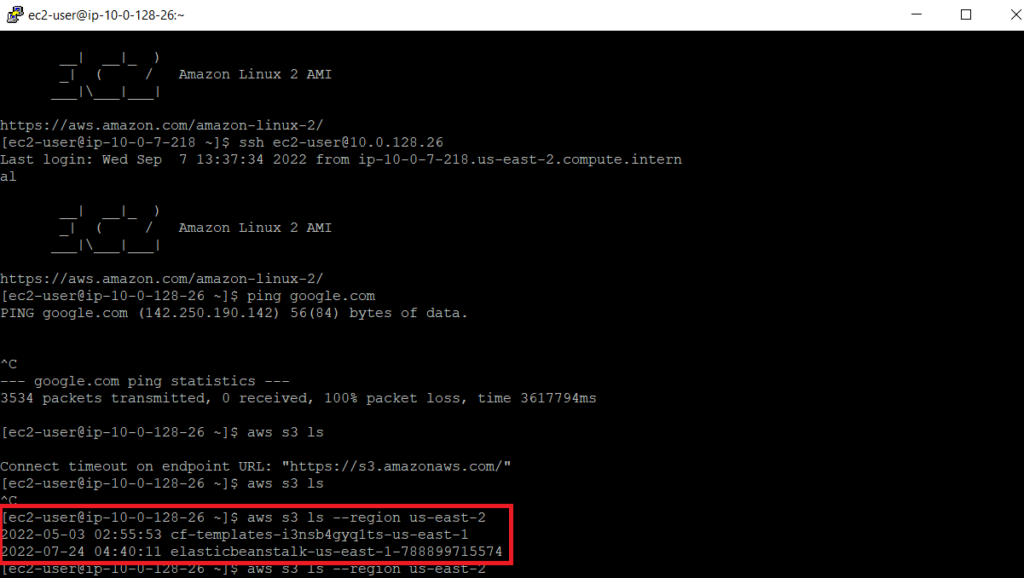
Conclusion
This tutorial walked you through setting up a more secure environment that allows you to access amazon’s S3 resources using their private network. This can help secure your environment since your private network will no longer need to reach the public internet to access aws resources.